While the internet has existed for several decades, it’s only in recent years that security has become a popular concern. Cybersecurity tools and products now are a multi-billion dollar industry. Security engineers and executives continue to mitigate risk by trying to accurately quantify where their organizations might be vulnerable.
Measuring security risk is hard. Typically, it isn’t until a breach occurs that an organization can fully understand the scope of cost of the damages. Vendor risk management platforms and cyber insurance are two examples of markets that assess the magnitude of damage while attempting to restore secure operations or making modifications to prevent future breaches.
Even after measuring the risk, there are myriad places waiting to absorb a security budget. Malicious actors have access to a trove of open source of tools and scripts. There is a subset of attacks that are executed by identifying a set of vulnerable banners or signatures.
A good analogy can be found in the Super Mario Brothers game. In the game, Mario gets to a castle, thinking he’s going to find the princess. Instead, he comes to find out that an imposter has been placed there as a diversion. A lightning rod, for example, diverts a potentially destructive power to some other target to neutralize the effect.
Let’s say for example you have a web server on your network serving up a website. You can inspect the HTTP headers by executing a simple request. (See Figure 1)
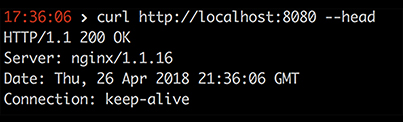
In this case, the web server is providing the version number, which is vulnerable to attack
(https://www.cvedetails.com/cve/CVE-2012-1180). If this information was hidden or changed to something less descriptive, an attacker might skip the IP because it doesn’t match some intended criteria.
Defenders can exploit this behavior by causing the attacker to spend more time focusing on a target that appears to be vulnerable, but actually isn’t. By loading up a series of possible headers that are vulnerable, automated attack scripts are kept guessing as to what the system might be without it ever actually being what it purports to be.
In a world where more home products are becoming connected (IoT devices), attackers seek to capture the IoT devices’ signatures. The Mirai botnet attack leveraged fingerprinted IoT devices by correlating them to factory default usernames and passwords, and thus gaining control over them. Once a set of IoT devices is under the control of a botnet, they can be used to initiate a massive global denial of service attack that is difficult to defend against.
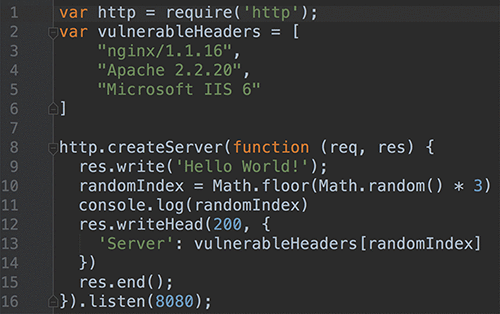
In the code snippet below (Figure 2) you’ll notice that an array of known vulnerable servers is loaded. One is randomly selected (it could be on a set timer) to return the response to the caller.
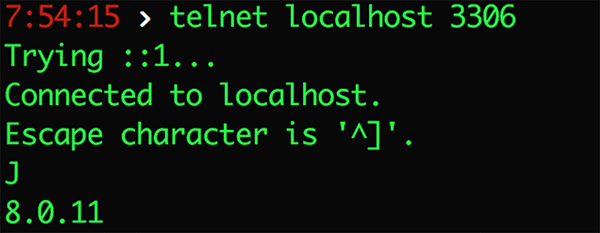
These services are sometimes described in terms of default network ports. Many popular applications have standard ports. For example port 5432 is PostgreSQL; MySQL is port 3306. From this designation one could also determine what version might serve over that port by opening a TCP network connection that would return what is called a “banner”.
As can be seen in figure 3, it’s easy to detect that the version of MySQL running is 8.0.11. Based on this knowledge, attacks to which this version might be vulnerable can be applied. On the defender’s converse side, this could be a false version banner, which causes the attack to be confused and waste time on something that could actually either be a different database or a not a database at all.
Keeping these types of services outside the firewall is generally bad practice. On the other hand, by having “fake” services showing as randomly available creates a lightning rod effect, sometimes called a honeypot, and creates a distraction or diversion from the actual services being protected. Another defense mechanism is the use of floating IPs. There are a number of ways to accomplish this (including using a content delivery network (CDN) or some other kind of load balancer). Again, the idea is to deceive the attacker by creating deception through uncertainty.
It’s even feasible to build an entire decoy network with a series of firewalls and instances that appear to be legitimate. Think of it as an entire building that appears to be somewhat locked down. Locked down enough to not appear as being fake, but open enough for someone with respectable black hat skills. They make their way through the structure unlocking rooms and passageways, but they never quite make it to the end as the infrastructure is constantly changing, creating a changing maze effect. Network components and software technologies are continuously changing causing the attacker further confusion.
So far, we’ve covered ways to deal with the application surface. Applications have certain signatures to them that make them discoverable. These signatures also create vulnerabilities. SQL for example, has certain syntactic nuances to them that make it noticeable to injection attacks (SQLi). Swapping the underlying database structure through an export function, however, can keep an attacker guessing.
On the web application side, a PHP handler could be built to serving a Python application. This tricks an attacker into sending PHP based payloads to an application that isn’t capable of understanding or executing them.
Moving Target Defense (MTD) builds on the idea of using a constantly changing environment to deceive an attacker. Imagine someone breaking into your house. They might be looking into drawers for valuables. What if you had a safe out in the open that had nothing in it. They might take the safe and just leave, because they believed that they had found what they were looking for. Bringing that analogy back to cybersecurity, one could have an application that returns fake passwords. The attackers think they’ve hit the jackpot, and leave. Alternately, an open SQL endpoint that looks like it’s connected to some notional PII (personally identifiable information). (Figure 4)
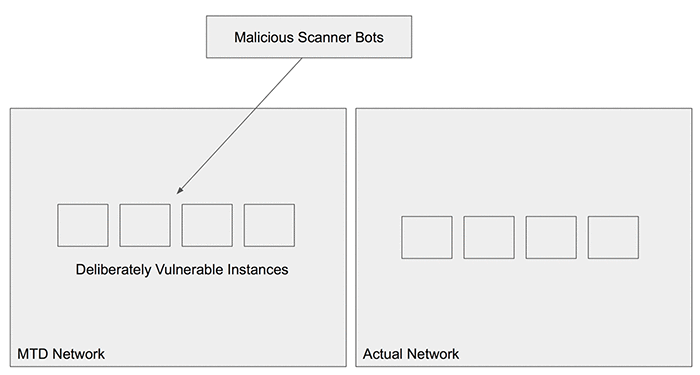
Deeper integrations of MTD are starting to appear. Malware infections rely on being able to fingerprint elements of an operating system. More sophisticated attacks reach into memory address spaces that can either read or corrupt (write) valuable data. Dynamic compilation mechanisms attempt to scramble those allocations. A Linux distribution claiming to be “polymorphic Linux” has appeared. The idea behind this effort is to hot swap packages and handle memory swapping at the kernel level. This type of holistic out of the box solution is a testament to the game changing value of moving target defense.
The internet war continues to rage, with malicious actors continuing to score significant victories, and security defense and damages cost continuing to rise. While cyber insurance might be a viable short-term mitigation strategy, more needs to be done with respect to how systems are designed and built. As Sun Tzu said in the Art of War “The supreme art of war is to subdue the enemy without fighting.” A moving target defense strategy is a more effective and proactive strategy in the fight against an ever-evolving threat.
–Reprinted from US Cybersecurity Magazine.


